Introduction
IAM, or Identity and Access Management, is a vital service provided by Amazon Web Services (AWS) for controlling access to AWS resources securely. Moreover, it allows users to manage permissions for accessing various services and resources within their AWS environment. In this blog, you will explore more about IAM.
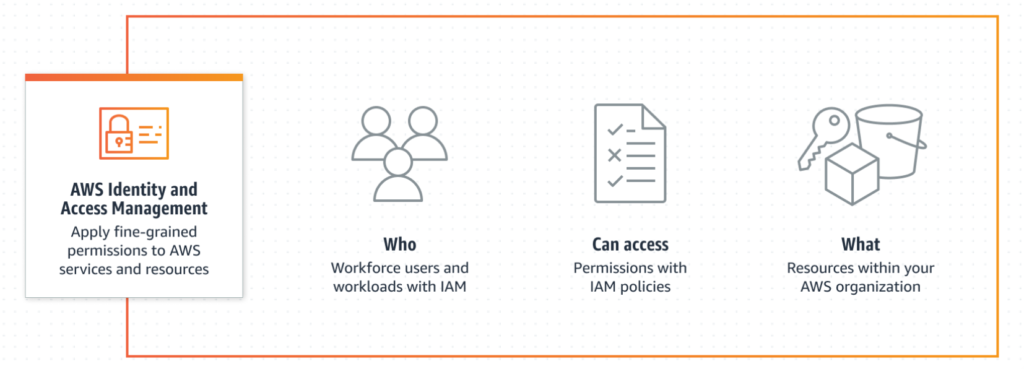
What is IAM?
IAM enables secure access and management of AWS resources and services. Additionally, with IAM, you can create and manage users, groups, and roles within your AWS account, defining permissions to control which users or entities can access specific resources and perform certain action.
Components of IAM
- Users: Representing individuals or services interacting with AWS resources, each user possesses unique security credentials and permissions.
- Groups: Collections of IAM users for streamlined permission management. Permissions are assigned to groups rather than individual users, facilitating efficient access control for similar tasks.
- Roles: Various entities, including AWS services, applications, or users from external AWS accounts, assume roles. Moreover, these roles define specific permissions and can be temporarily assumed by trusted entities.
- Policies: JSON documents specifying permissions. Users, groups, or roles can attach policies, dictating allowed or denied actions on specific AWS resources. Moreover, these policies enable fine-grained control over access permissions within an AWS environment.
Features of IAM
- Identity Management: IAM enables you to create and manage users and groups, providing unique security credentials for each user.
- Access Control: IAM allows you to define fine-grained access policies to control who can access specific AWS resources and what actions they can perform.
- Role-based Access Control (RBAC): IAM supports the concept of roles, allowing you to assign permissions to roles and then assign these roles to users or AWS services.
- Granular Permissions Using IAM policies, you can define permissions at a granular level, specifying which actions are allowed or denied for specific AWS resources.
- Multi-factor Authentication (MFA): IAM supports MFA, adding an extra layer of security by requiring users to provide an additional authentication factor, such as a one-time password generated by a hardware or virtual MFA device.
- Identity Federation: It enables you to federate identities from external identity providers, thus allowing users to access AWS resources using their existing credentials.
- Access Key Management: It allows you to create and manage access keys for programmatic access to AWS services, ensuring secure authentication for APIs and CLI usage.
- Audit and Logging: IAM integrates with AWS CloudTrail to provide detailed logs of user activity and API calls. Furthermore, this integration helps you monitor and audit access to your AWS resources.
- Resource-based Policies: You can attach IAM policies directly to AWS resources, thus enabling you to control access to those resources without needing to manage individual user permissions.
Conclusion
Amazon Web Services offers AWS IAM as a fundamental service for managing user identities and controlling access to AWS resources. Additionally, with features like granular permissions, identity management, and access key management, IAM plays a crucial role in ensuring the security and efficiency of AWS environments.
Also read our blog post on AWS CloudFormation.
What’s Next?
“We’re here to support you! Should you have any questions or need assistance, don’t hesitate to get in touch with us. Contact us at info@uranuscloudsolutions.com and we’ll be happy to help. Your satisfaction is our priority!”.