Introduction
AWS is a top leading cloud provider that offers a powerful tool to secure your cloud infrastructure known as AWS IAM (Identity and Access Management). AWS IAM allows you to manage access to AWS resources. In this blog, we’ll delve into the key features of AWS IAM, its benefit and the best practices for using it effectively.
What is AWS IAM?
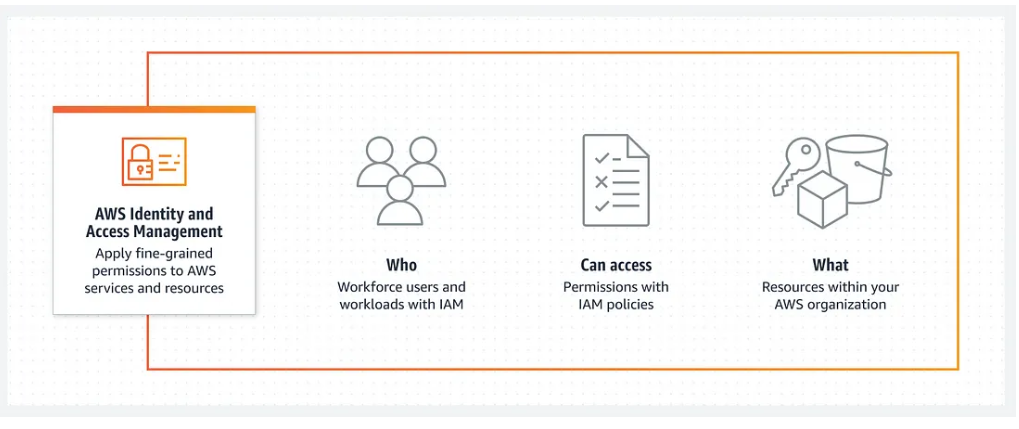
AWS IAM stands for Identity and Access Management. It is one of the foundational services in AWS that enables you to manage access to AWS resources securely. Moreover, IAM allows you to create and manage AWS users and groups, and use permissions to allow or deny their access to AWS resources.
Key Features
- Granular Permission: IAM lets you define fine-grained permissions, specifying which users or roles can access particular resources and what actions they can take. By following the principle of least privilege, it ensures that users have only the necessary access they need.
- Users: Individual identities that you create in AWS IAM. Each user has unique credentials, including a username and password, or access keys for programmatic access.
- Groups: A collection of users is called a group, which helps simplify permission management by applying the same policies to multiple users at once.
- IAM Roles: IAM Roles are sets of permissions that can be assumed by users, applications, or AWS services.
- Multi-Factor Authentication (MFA): MFA (Multi-Factor Authentication) means an additional layer of security that requires users to provide a second form of verification in addition to their password. It helps protect against unauthorized access, even if passwords are compromised.
- AWS Managed Policies: AWS provides pre-defined policies to simplify the process of granting permissions.
- Custom Policies: For advanced use cases, IAM allows the creation of custom policies tailored to specific needs.
Benefits
- Cost Management: IAM helps manage costs by controlling who can create or modify resource.
- Security: IAM ensures that only authorized individuals and services can access AWS resources, reducing the risk of data breaches and unauthorized activities.
- Compliance: IAM not only allows organizations to enforce security policies and audit access, thereby helping to meet regulatory requirements and maintain compliance with industry standards.
- Scalability: IAM’s flexible design facilitates the efficient management of permissions as your organization grows, ensuring that security scales with your expanding cloud infrastructure.
Best Practices
- Apply the Principle of Least Privilege
- Enable MFA for All Users
- Implement Resource-Based Policies
- Use IAM Roles for Applications
Conclusion
AWS IAM is an essential tool for any organization using AWS. By understanding its benefits and following best practices, you can build a strong security framework that safeguards your cloud resources while enabling efficient management.
Also read our blog post on AWS Network Security.
What’s Next?
We’re here to support you! Should you have any questions or need assistance, don’t hesitate to get in touch with us. Contact us at info@uranuscloudsolutions.com and we’ll be happy to help. Your satisfaction is our priority!.